MilliSec Endpoint Security
Comprehensive protection for all network endpoints.
We protect workstations, servers and local networks from viruses, malicious software and unauthorized access.
Description
MilliSec Endpoint Security is a powerful endpoint protection tool. It controls access, monitors system events, detects and prevents threats. The built-in monitoring mechanism records suspicious activity, while the access control system helps prevent unauthorized use of corporate data.
The solution is designed for businesses, government structures, and critical infrastructures. It reduces cybersecurity risks, protects confidential data, and helps meet regulatory requirements. With MilliSec Endpoint Security, information remains under control and devices stay secure.
What does MilliSec Endpoint Security do?
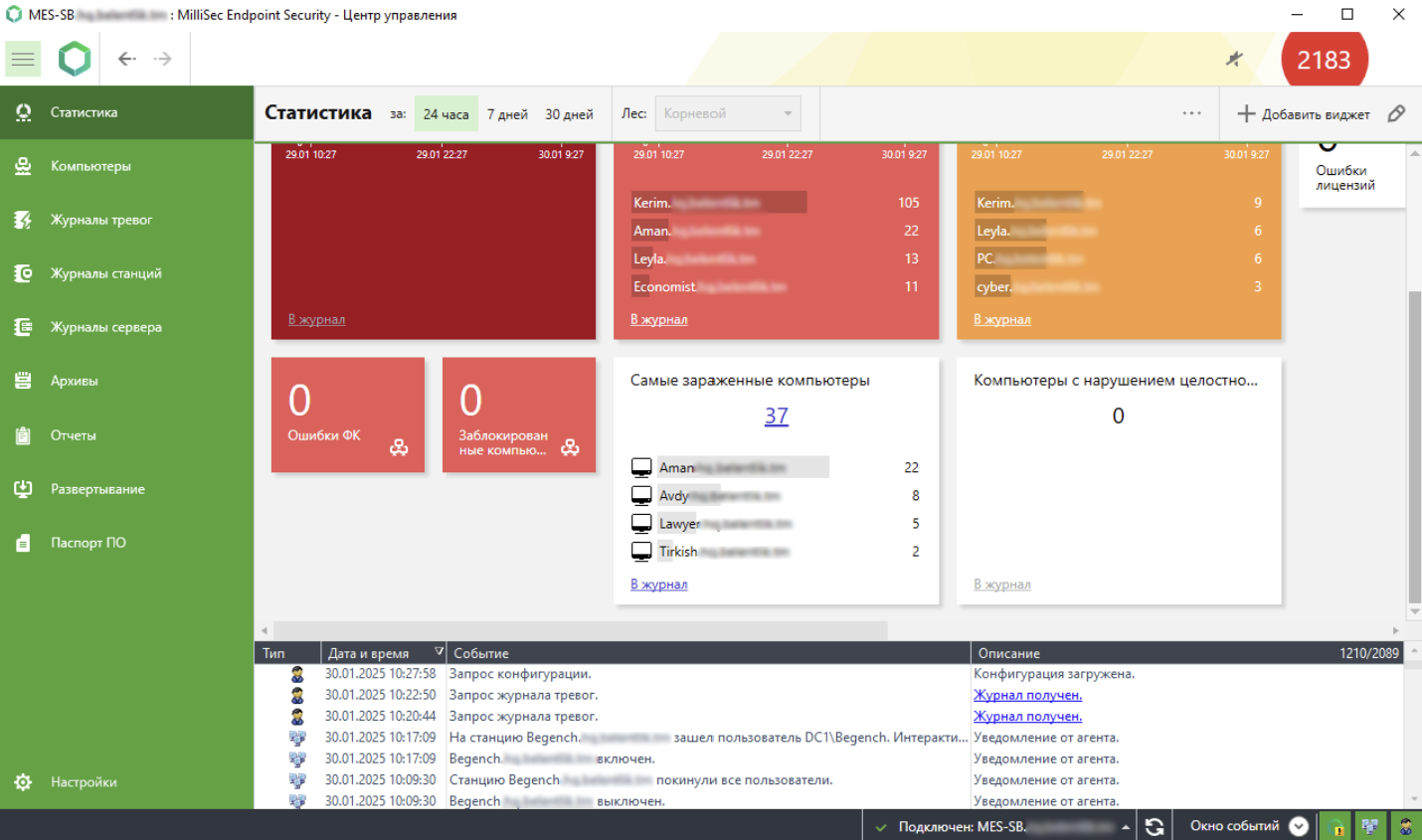
Advantages
Government Structures
cybersecurity of information systems.
Industry
protection of technologies and industrial systems from external attacks.
Large Business
internal security control and employee monitoring.
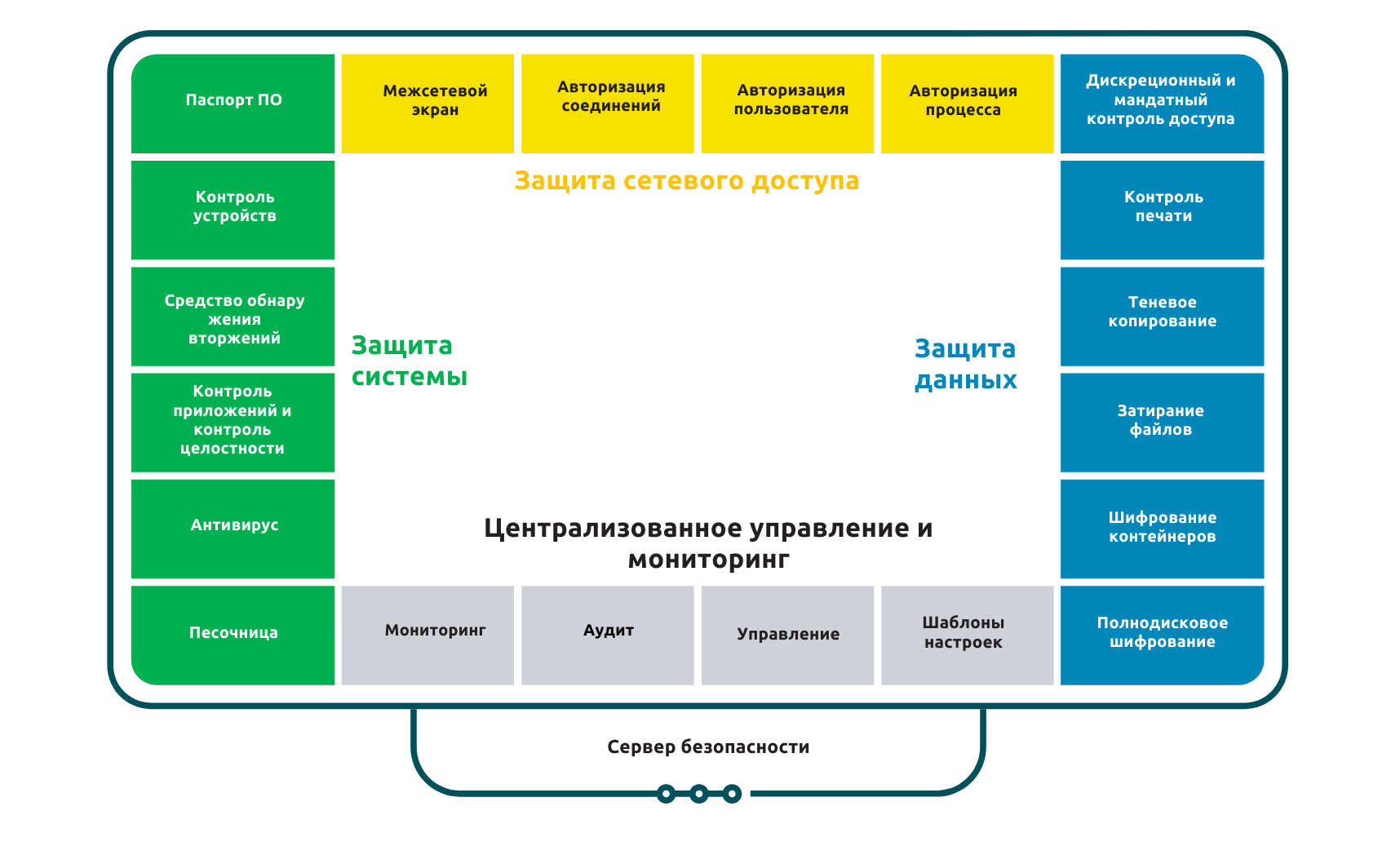
Key Features
Why choose us?
01
Complete protection of workstations and servers. Your data remains securely protected thanks to antivirus monitoring, application control, and document shadow copying. This helps secure corporate networks.
02
Access control at all levels. Flexible mandatory and discretionary control mechanisms allow restricting access to confidential information, ensuring that only authorized users can work with important data.
03
Network connection security. Built-in firewall and attack protection prevent unauthorized access and protect network traffic from spoofing and interception.
04
Enhanced authentication. Multi-factor authorization support ensures secure system login even in critical environments.
05
Centralized management and audit. Flexible centralized management system allows administrators to configure security policies, monitor user activity, and receive timely notifications of suspicious events.